In this Episode of the Brief we had the pleasure of sitting down with Faud Khan – Founder and Chief Security Analyst at TwelveDot. In case you’re not familiar with TwelveDot, they work in the cyber security space and are dedicated to bringing a global perspective to security. Faud himself could be considered somewhat a veteran in the industry with over 20 years of IT security experience and a growing portfolio of international clients and services. Currently, his focus lies in mobile, cloud and IoT security.
…Now that we’ve ‘met’ the expert, let’s begin with the basics by understanding the threats –
“Privacy 20 years ago wasn’t the issue it is today… Today, the things you thought were hidden are now exposed.” – Faud Khan

Cyber security and more recent data breaches have become a growing concern across the board, and the reason why is – the concept of openness. Openness refers to the fact that many individuals want to share data publicly on personal and/or commercial levels. This includes who you’re meeting, where you’re meeting and the tracking details that go along with this (such as your geo location). Now, it gets a bit clouded when you realize that companies who you trust with this collected data may be selling it for profit and may not be storing it securely. There are instances when data accessibility can pose major security threats to people and businesses. Without a methodical and process driven approach to cyber security you may be at risk of a security breach.
When it comes to business there must a balance between shared and secured data. Enough data has to be shared so that you are searchable, but on the other hand, a compromise of data could cost you your privacy, your job, or your business. New digital fingerprints are being created everyday and we don’t necessarily have control if they’re being used for good or bad, so don’t be a target, be prepared for the day a breach happens.
There’s a breach. Who is responsible?
The lag in education on cyber security puts organizations at risk and execs on the hook. The key to effectively protecting ourselves is to be geared for action before the threat even presents itself. When it comes to a breache the idea is to be acting, not reacting and as everything is connected, everything should be protected. With the rise of hacktivism and cyber crime, the guarding of our confidential data is more important than ever. Our devices are getting smarter, and subsequently, so are people. As such, social engineering is the greatest cause for breach organizations. It’s allowing users with bad intentions to gain access to people and systems, allowing malefactors to take hold of your personal data for the purpose of using it distinctly against you or selling your confidential data. Consumers need to protect themselves, and so do businesses. The only way to do this is through threat modelling. Threat modeling zeros in the weaknesses of a system design and process and provides the necessary inputs for a cyber security strategy. It identifies risks and exposures and possible mechanisms to secure your solution solutions and establishes strategies to do so. It looks at scaling your exposure at the inception of your application to better prepare you for what’s targeting you.
Threat Profiling and hacktivism: what does it all mean?
Hacktivism is a growing trend. More and more people have been making use of the web to express anger, or even steal data. With sites that sell zero-day and DoS tools for cheap, it becomes a way to state your opinion about a company or organization from the comfort of your living room. It’s proved itself dangerous for many, and has opened up pot holes for most. Yet another threat that we need to protect ourselves from, while opening up a whole new can of worms for cyber security. This is where the importance of threat profiling prevails. Threat profiling aims to evaluate company assets and assess both the potential goals and outcomes of the attacker. Though threats against your organization can be accidental or deliberate, above all, they are compromising. Profiling allows for us to plan, train and develop strategies for risk mitigation. Creating a threat profile means understanding your organization’s vulnerabilities and protecting yourselves accordingly!
Policies and Procedures
When it comes to cyber security it’s extremely important for a company to understand where they may have weakness in their security and have a plan to reprimand those gaps. Thus, implementing an information security management system ISMS to ensure that policies and procedures align to corporate objectives is a must! This investment in an ISMS will help prepare a company for its future. A typical ISMS plan follows the following cycle:
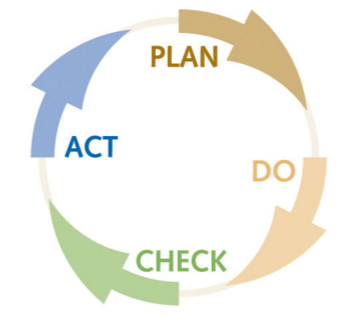 1: The Plan phase is about designing the ISMS, assessing information security risks and selecting appropriate controls.
1: The Plan phase is about designing the ISMS, assessing information security risks and selecting appropriate controls.
- 2: The Do phase involves implementing and operating the controls.
- 3: The Check phase objective is to review and evaluate the performance (efficiency and effectiveness) of the ISMS.
- 4: The Act phase, changes are made where necessary to bring the ISMS back to peak performance.
The message is clear: security is important to your brand. The question is what do organizations need to be thinking about today to protect their critical data tomorrow ? If you need some help painting that picture, contact me or reach out to the experts at TwelveDot <http://twelvedot.com/contact-us/> to start your security project, or connect on the latest security topics affecting your business.
Skip to sharing